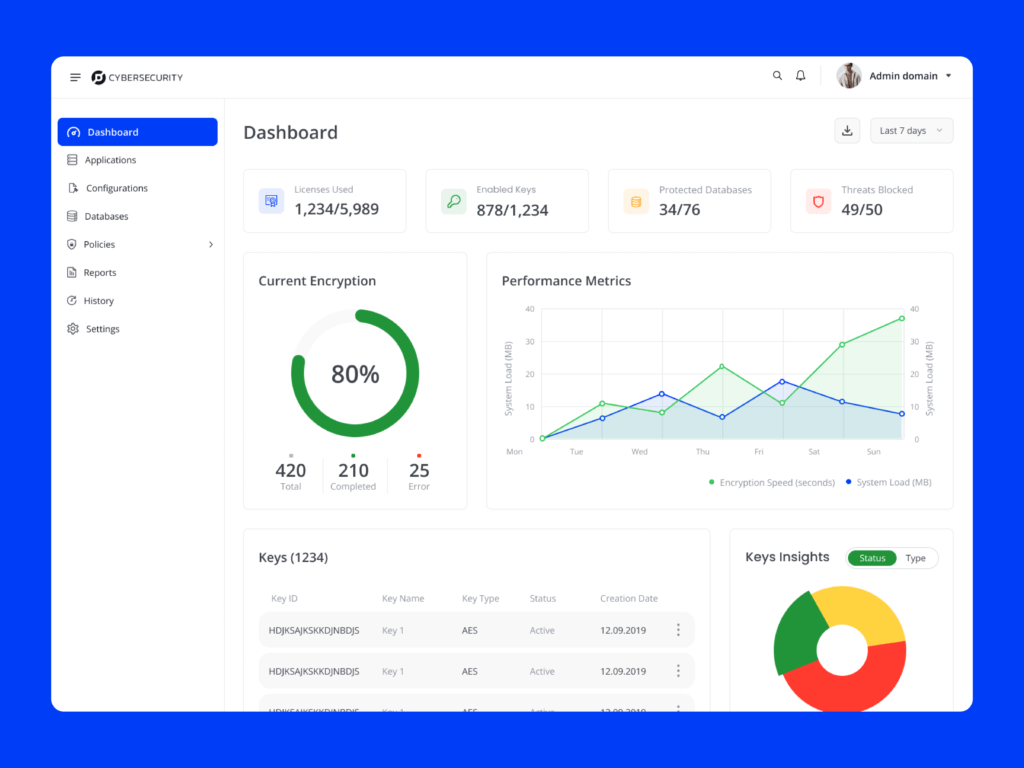
With phishing attacks accounting for nearly 90% of data breaches worldwide, security design has become more critical than ever for protecting users and organizations. The challenge lies in creating interfaces that users trust and can easily navigate while maintaining robust protection against sophisticated cyber threats.
In fact, our experience shows that users typically notice design elements before considering security features. However, this doesn’t mean we must compromise one for the other. Through our journey of developing a cybersecurity app, we discovered how to implement security by design principles that satisfy both requirements. This article shares our practical insights on transforming complex cyber security design into simple, user-friendly solutions that effectively protect against modern threats.
Identifying the Core Security Design Challenges
Our initial research into security design revealed that large organizations use more than 130 security tools on average, creating a complex web of protection that often hinders rather than helps.
Initial user research findings
Research shows that users primarily struggle with password management and authentication processes. Additionally, workplace security policies often impose more than 10 distinct rules on users, making it challenging to maintain compliance across multiple systems. Notably, users express concerns about forgetting authentication credentials and dealing with session timeouts, even when sitting at their desks.
Common pain points in security interfaces
Users face several critical challenges in security interfaces. Research indicates that enterprise applications frequently suffer from complicated linear flows, making navigation unnecessarily complex. Furthermore, security professionals often prioritize system integrity over user experience, consequently creating interfaces that feel cumbersome and unintuitive.
The most significant pain points include:
• Cluttered interfaces that overwhelm users with excessive information
• Complex navigation structures that lead to user frustration
• Difficulty understanding information hierarchy in security settings
Key areas requiring simplification
Our analysis identified that security design requires simplification in several crucial areas. Primarily, the traditional perimeter-based approach to security no longer suffices, as modern IT environments span across on-premises, cloud, and hybrid systems. Research demonstrates that organizations need to focus on consolidating security tools and working with fewer, more versatile vendors. Additionally, the integration of security measures must consider human behavior patterns, as users often circumvent overly complex security mechanisms.
Our Security by Design Approach
Building secure products starts with incorporating security measures from the ground up. Our approach focuses on creating technology products that protect against malicious cyber actors through thoughtful design and implementation.
Establishing design principles
We established three fundamental security design principles to guide our development process. Primarily, we focused on making security features available without additional cost. Therefore, we implemented a “secure by default” approach where products automatically enable critical security controls. Essentially, we shifted the burden of security configuration from users to manufacturers.
Creating user-centered security flows
Since security cannot be bolted on later, we integrated security measures throughout the development lifecycle. Our user-centered approach focuses on creating intuitive experiences that don’t overwhelm users with security options initially. Accordingly, we implemented a simple three-level security slider with a pre-selected “recommended” middle option.
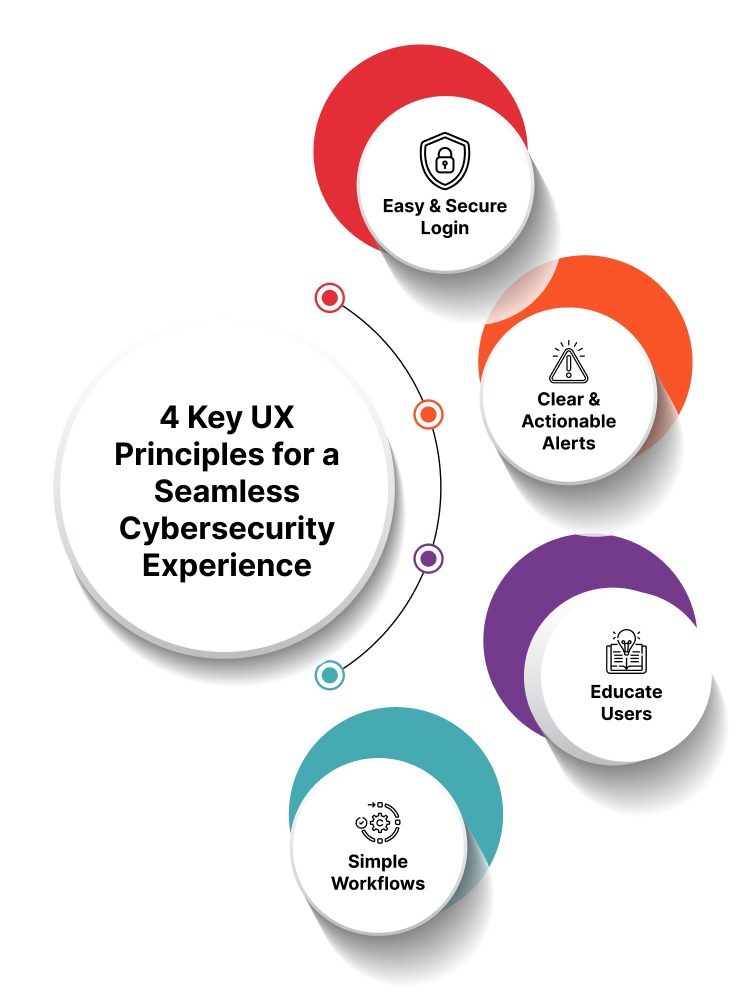
Educating Through UX
Security is most effective when users understand the risks and know how to respond. Instead of overwhelming users with technical jargon, integrate security education directly into the interface through tooltips, step-by-step guidance, and real-time alerts. Providing clear explanations for security decisions and offering proactive recommendations empowers users to make informed choices, reducing errors and improving overall cybersecurity awareness.
Continuous Security Feedback
Users should always feel in control of their security without being overwhelmed. Providing real-time feedback on security actions, such as confirmation messages after enabling two-factor authentication or visual indicators for secure connections, builds trust and confidence. Regular but non-intrusive updates about security status help users stay informed without disrupting their experience.
Balancing security and usability
Although robust security is crucial, we recognized that overly complex measures often lead users to create workarounds. Thus, we divided our application into sensitive and low-security areas, requiring strong authentication only where necessary. For everyday tasks like viewing content, we simplified the security requirements while maintaining protection.
To enhance user trust, we implemented clear visual indicators showing login status on every page. Similarly, we automated 90% of verification processes, only requesting user interaction for suspicious activities like logging in from new devices. This approach ensures both security and seamless user experience without compromising either aspect.
Iterative Design Process and Testing
Developing secure applications demands rigorous testing and continuous refinement. Our prototype development process specifically focuses on identifying and addressing security vulnerabilities early in the development cycle.
Prototype development stages
The development process begins with quick design phases based on initial requirements. Subsequently, we create preliminary prototypes that showcase core functionality and security features. Each prototype undergoes thorough security validation, primarily focusing on API vulnerabilities and communication channels.
User testing methodology
Our testing approach combines automated vulnerability scanning with manual penetration testing to create comprehensive security assessments. Specifically, we employ guerrilla testing, where testers approach random users in public spaces for quick 5-10 minute feedback sessions. Moreover, we conduct screen recording sessions with 10 users for 15-minute intervals to understand their interaction patterns.
Incorporating feedback loops
The feedback process involves collecting user responses from multiple platforms, including social media, review sites, and online forums. We analyze this information to identify:
• Security usability issues
• Interface navigation challenges
• Authentication pain points
• Performance bottlenecks
Indeed, our feedback loops have proven invaluable for enhancing application security. The process helps developers catch potential vulnerabilities early, ultimately reducing the probability that larger user groups will encounter serious bugs or usability issues. Meanwhile, we maintain continuous communication with users about new updates and improvements, establishing trust and fostering a loyal user base.
Through this iterative approach, we’ve created a system where security testing becomes an integral part of the development lifecycle. The process ensures that each code change undergoes automated security checks before merging, establishing a robust foundation for ongoing security improvements.
Measuring Success and Impact
Tracking the right metrics proves vital for evaluating security design effectiveness. Our comprehensive measurement framework focuses on both technical performance and user experience aspects.
Key performance metrics
Tracking security incidents reveals crucial insights about system effectiveness. Primarily, we monitor three critical timing metrics: Mean Time to Detect (MTTD), Mean Time to Resolve (MTTR), and Mean Time to Contain (MTTC). Overall, these measurements help identify gaps in defenses and ensure quick response to potential threats.
For system security assurance, we track:
• Patching cadence and effectiveness
• Access management controls
• Third-party vendor security ratings
• Incident response automation
User adoption rates
User satisfaction directly correlates with effective security implementation. Particularly, our measurements show higher adoption rates when security controls align with user expectations and work processes. The implementation index indicates that streamlined setup processes and intuitive administrative tools lead to increased user engagement.
Security features that enhance information quality, system responsiveness, and support services generate significantly higher user satisfaction scores. Evidently, when users understand the benefits of security practices while maintaining their productivity, adoption rates improve substantially.
Security compliance improvements
Generally, successful security compliance depends on both technical components and proper user interaction. Our monitoring shows that organizations implementing security-by-design principles experience better compliance rates and reduced operational costs.
The data indicates that users comprehend the importance of security practices but remain cautious about overly complex controls. By focusing on user-friendly security measures, we’ve observed improved compliance rates across various security protocols. Furthermore, automated security checks and detailed logging capabilities have strengthened our compliance monitoring system.
Conclusion
Security design presents a delicate balance between robust protection and user-friendly experiences. Through our journey developing this cybersecurity app, we demonstrated that complex security measures can become simple, intuitive solutions without compromising protection.
Our user-centered approach, combined with security-by-design principles, yielded remarkable results. Rather than overwhelming users with numerous controls, we simplified interfaces while maintaining strong protection. This strategy proved effective as shown by improved adoption rates and enhanced compliance metrics.
The success of our iterative design process validates an important lesson: security features work best when users understand and embrace them naturally. Organizations looking to strengthen their security measures should consider that simplicity often leads to better protection than complexity.
Security design will continue evolving as threats become more sophisticated. Nevertheless, our experience shows that focusing on user needs while maintaining robust protection creates lasting solutions that users actually want to use. This approach not only strengthens security but also builds trust and encourages consistent engagement with security features.