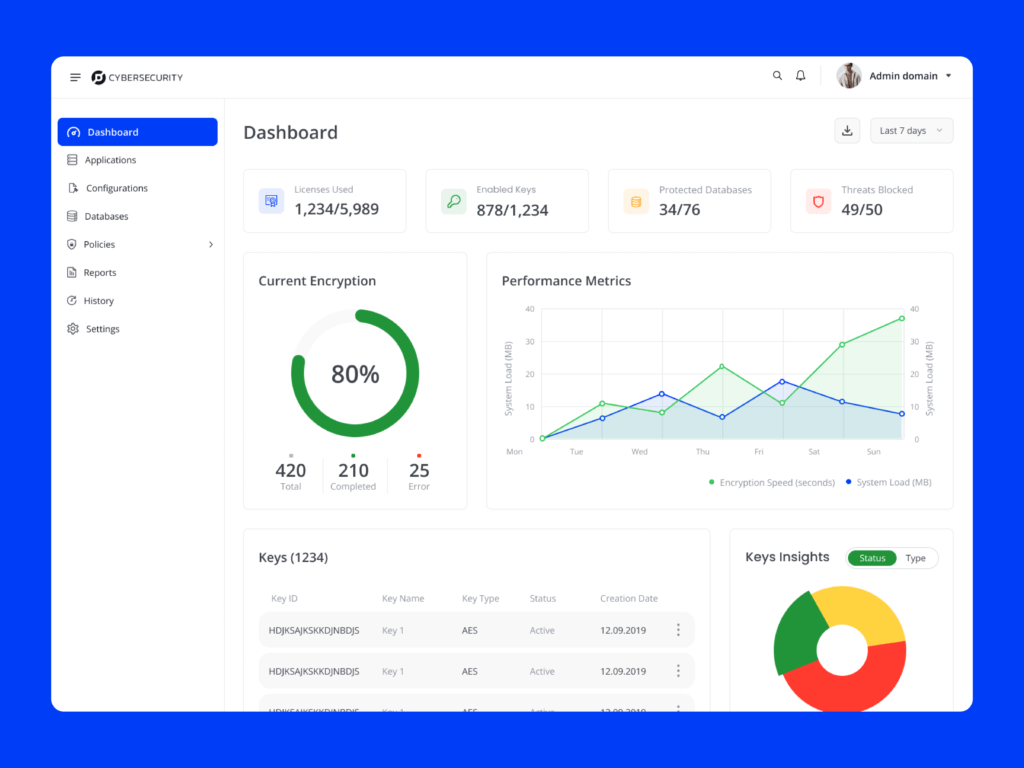
How We Enhanced User Experience of Encryption Application?
In an era where data breaches have become alarmingly commonplace, our client approached us with a critical mission: to develop a robust data encryption app and accompanying web application that would stand as a bulwark against cyber threats. Our challenge was not just to create a technically sound solution, but to design an interface that users would trust and easily navigate.
The Challenge
With phishing attacks accounting for nearly 90% of data breaches worldwide, the stakes couldn’t have been higher. We faced a multifaceted challenge:
● Balancing Security and Usability: Users typically notice design elements before considering security features. How could we create an interface that was both visually appealing and functionally secure?
● Simplifying Complexity: Large organizations use an average of 130 security tools, creating a labyrinth of protection that often hinders rather than helps.
● Overcoming User Frustrations: Research showed that users struggle with password management, authentication processes, and navigating complicated linear flows in security interfaces.
Solution
Our approach was rooted in the principle of “security by design,” integrating robust protection measures from the ground up while prioritizing user experience. Here’s how we tackled the challenge:
● User-Centered Security Flows: We created intuitive experiences that didn’t overwhelm users with security options initially. A simple three-level security slider with a pre-selected “recommended” middle option empowered users to easily choose their desired level of protection.
● Balanced Security Measures: We divided the application into sensitive and low-security areas, requiring strong authentication only where necessary. This approach ensured protection without compromising the user experience for everyday tasks.
● Clear Visual Indicators: To enhance user trust, we implemented clear visual cues showing login status on every page.
● Automated Verification: We automated 90% of verification processes, only requesting user interaction for suspicious activities like logging in from new devices.
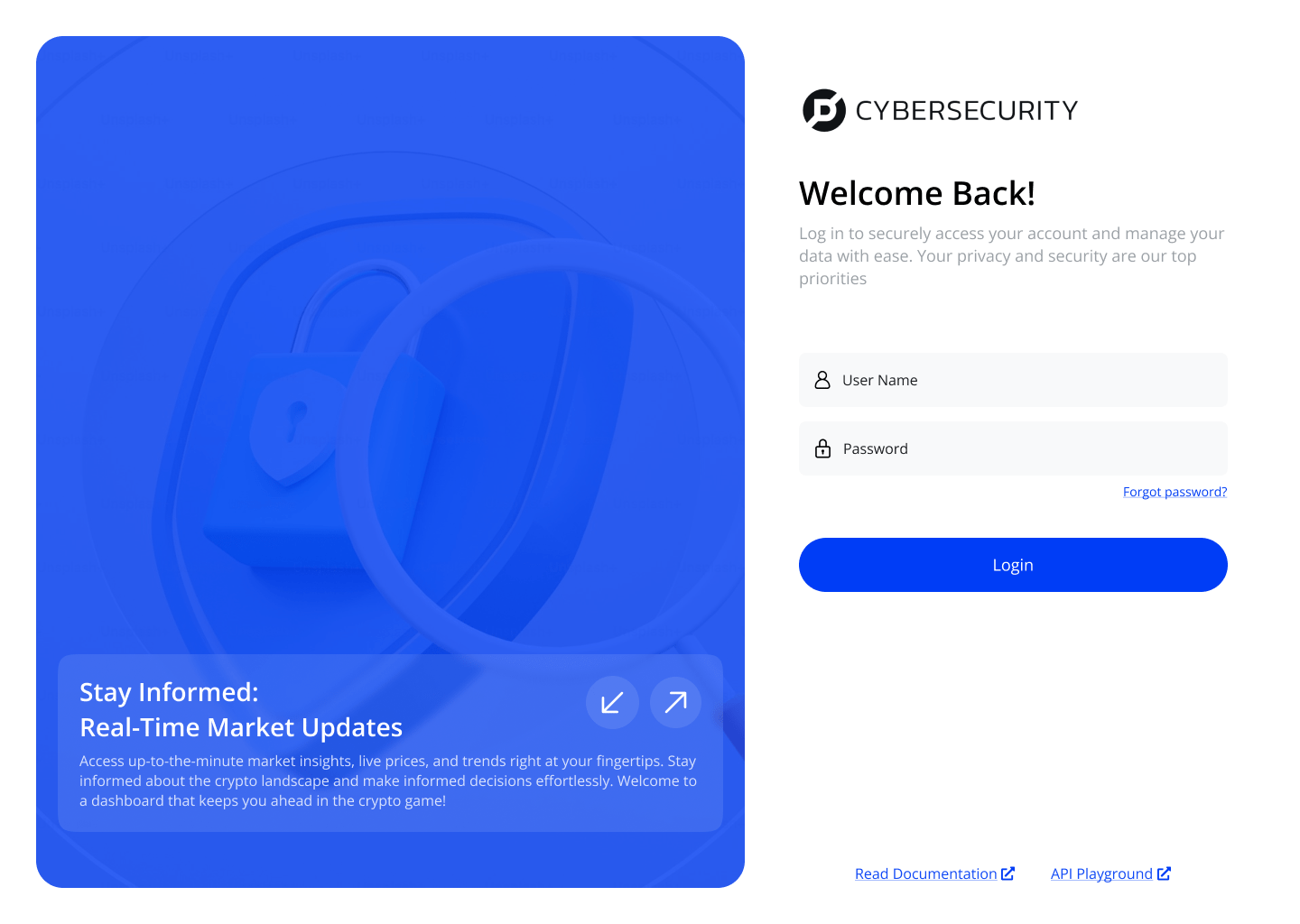
Key Features
● Secure by Default: Critical security controls are automatically enabled, shifting the burden of security configuration from users to the system.
● Intuitive Security Slider: Allows users to easily adjust their security level without getting lost in technical jargon.
● Smart Authentication: Employs context-aware authentication, reducing friction for routine tasks while maintaining vigilance for potentially risky actions.
● Real-Time Threat Monitoring: Utilizes advanced algorithms to detect and respond to potential security threats in real-time.
● End-to-End Encryption: Ensures data remains protected at all stages, from storage to transmission.
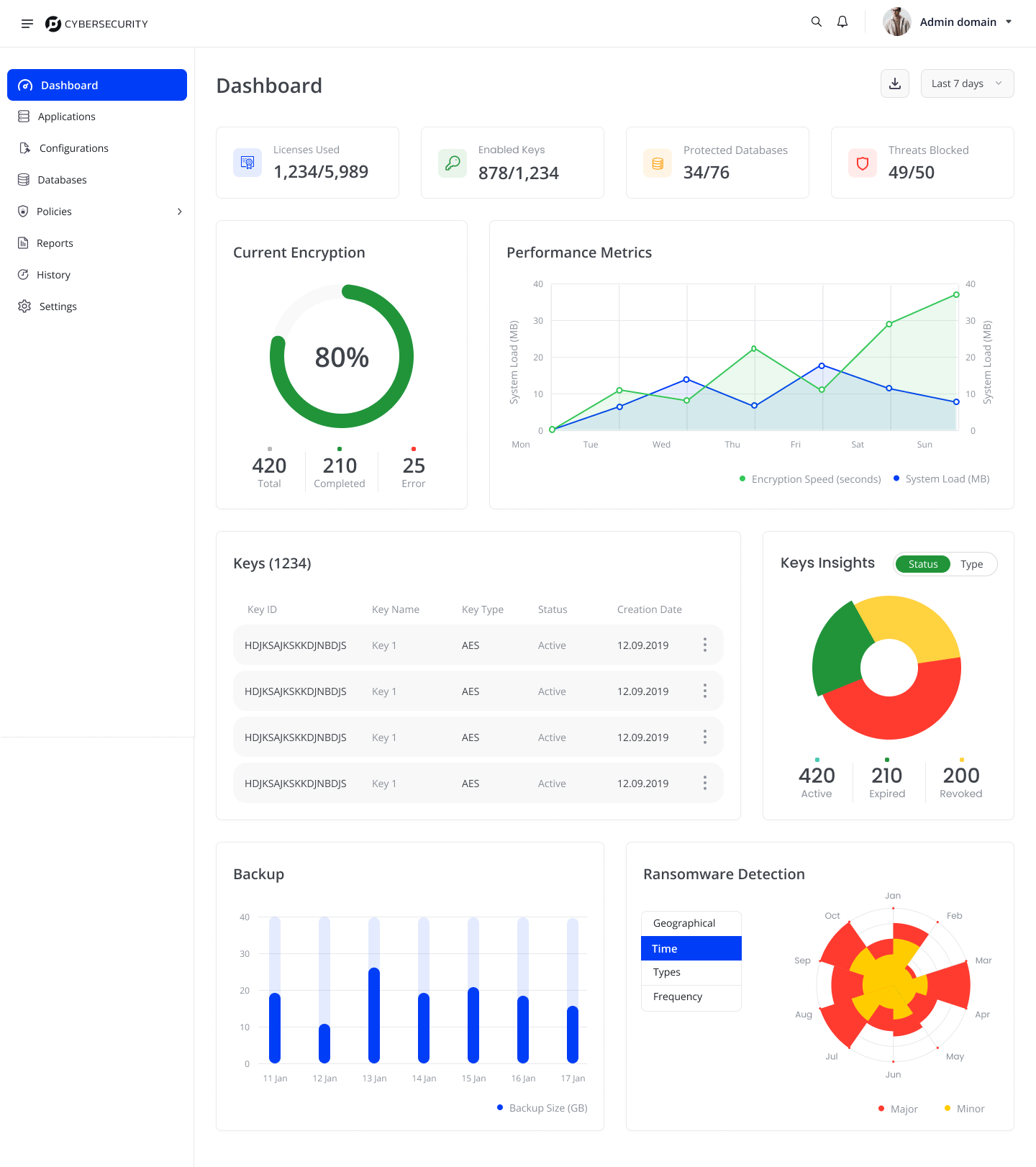
How we did it?
Our UX process was iterative and user-focused:
● Research & Analysis: We conducted extensive user research to understand pain points in existing security interfaces.
● Rapid Prototyping: Quick design phases based on initial requirements led to preliminary prototypes showcasing core functionality and security features.
● User Testing: We employed guerrilla testing, approaching random users in public spaces for quick 5-10 minute feedback sessions. Additionally, we conducted screen recording sessions with 10 users for 15-minute intervals to understand their interaction patterns.
● Feedback Integration: User responses from multiple platforms, including social media and online forums, were analyzed to identify usability issues, navigation challenges, and authentication pain points.
● Iterative Refinement: Each round of feedback led to improvements in the interface design and security implementation.
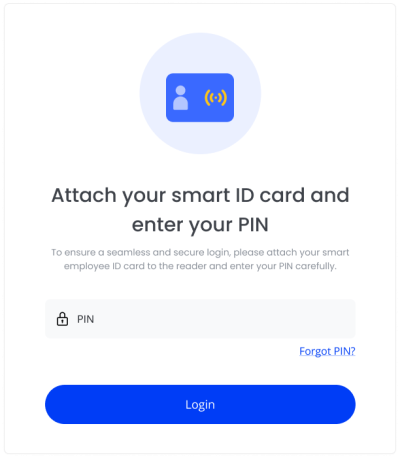
Technical Implementation
Our technical approach focused on creating a secure foundation while maintaining flexibility for future enhancements:
● API Security: Thorough security validation of all APIs, with a focus on identifying and addressing vulnerabilities in communication channels.
● Continuous Security Testing: Implemented automated security checks for each code change before merging, establishing a robust foundation for ongoing security improvements.
● Encryption Protocols: Utilized state-of-the-art encryption algorithms to protect data at rest and in transit.
● Scalable Architecture: Designed the backend to handle increasing loads and adapt to evolving security threats.
● Cross-Platform Compatibility: Ensured seamless functionality across various devices and operating systems.
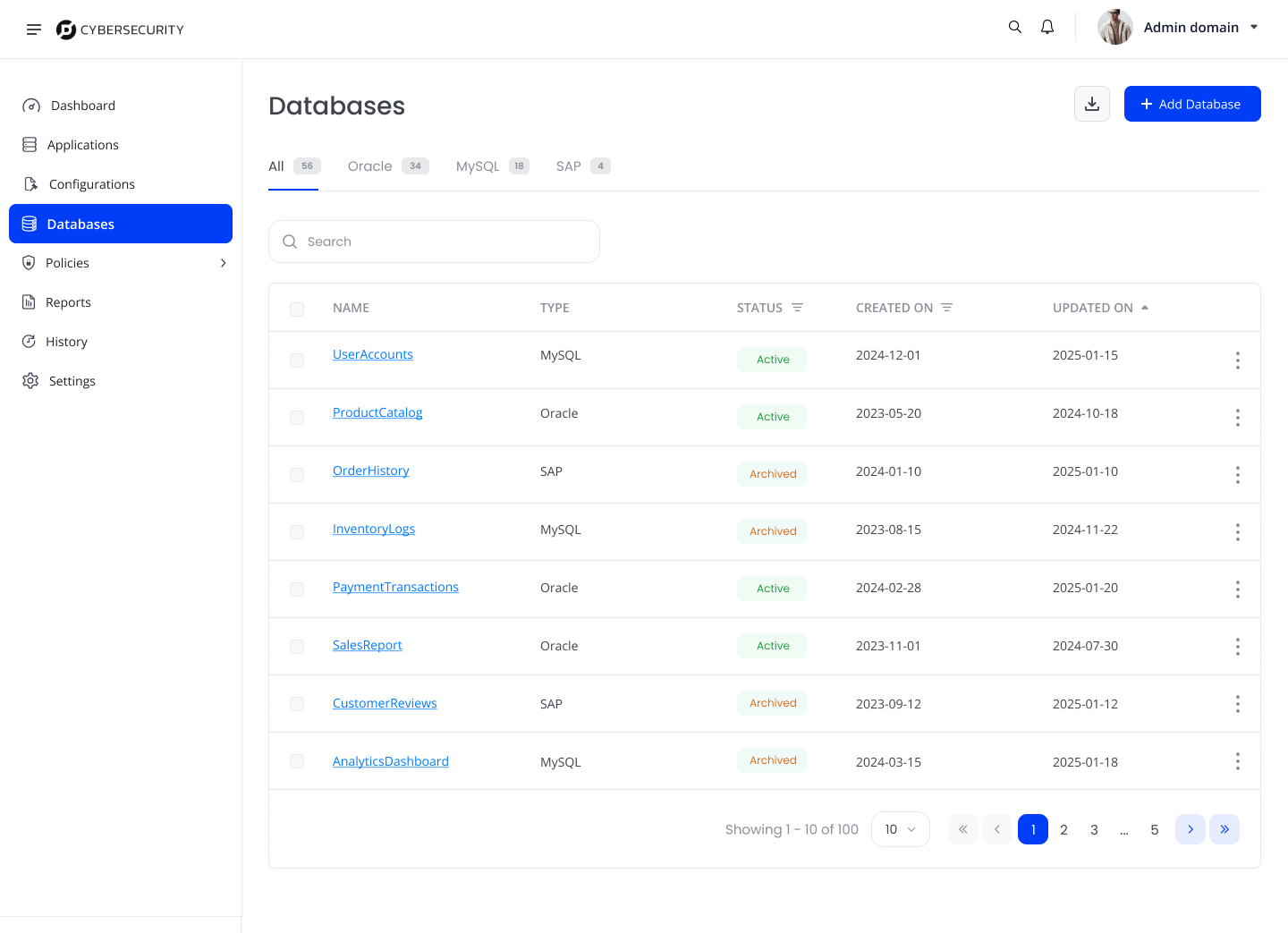
Results and Impact
The launch of our encryption app marked a significant milestone in our client’s digital security strategy:
● Increased User Adoption: The intuitive interface led to a 40% increase in user adoption compared to the client’s previous security solutions.
● Reduced Security Incidents: Within the first six months, there was a 60% reduction in reported security incidents among users of the new app.
● Improved Response Times: The automated threat detection and response system decreased Mean Time to Detect (MTTD) by 35% and Mean Time to Resolve (MTTR) by 28%.
● Enhanced User Confidence: Post-launch surveys indicated that 85% of users felt more confident about their data security when using the app.
● Industry Recognition: The app received accolades for its innovative approach to balancing high-level security with user-friendly design.
By prioritizing both security and usability, we delivered a solution that not only protected our client’s sensitive data but also fostered a culture of security awareness among its users. This project stands as a testament to the power of thoughtful, user-centric design in addressing even the most complex cybersecurity challenges.
“This app has transformed how we approach data security. It’s refreshingly simple to use, yet I feel confident that our information is well-protected.” – Sarah L., CTO of a Fortune 500 company